
(HedgeCo.Net) A fresh federal investigation into a possible hack of U.S. government digital-asset accounts is quickly becoming one of the most consequential “crypto operations” stories of early 2026—less because of the dollar value alleged, and more because of what it implies: the world’s most sophisticated law-enforcement apparatus may be running 21st-century assets on custody plumbing that was designed for a different era.
According to Reuters reporting that cited a Bloomberg report, the U.S. Marshals Service (USMS) confirmed it is investigating a possible compromise involving government-controlled crypto wallets. The agency declined to comment further while the investigation remains ongoing.
This is not a routine incident. The Marshals Service isn’t just “another agency that holds crypto.” It is the operational backbone for managing, securing, and ultimately disposing of cryptocurrencies seized or forfeited in federal cases—functionally, a key custody node for the U.S. government’s digital-asset pipeline.
What makes this investigation especially market-relevant is the convergence of three trends:
- More crypto is being seized, held, and managed by governments, often across multiple agencies and contractors.
- Hackers are getting paid more, faster, and with better laundering tools than ever before.
- Regulators are simultaneously trying to “normalize” crypto inside the financial system, which raises the stakes for custody, controls, and governance.
In other words: this investigation isn’t just about a wallet. It’s about whether digital assets are now systemically important enough that operational failures—inside institutions, inside platforms, or inside government—can reshape policy and market structure.
What We Know So Far: A Hack Claim Tied to Seizure Wallets:
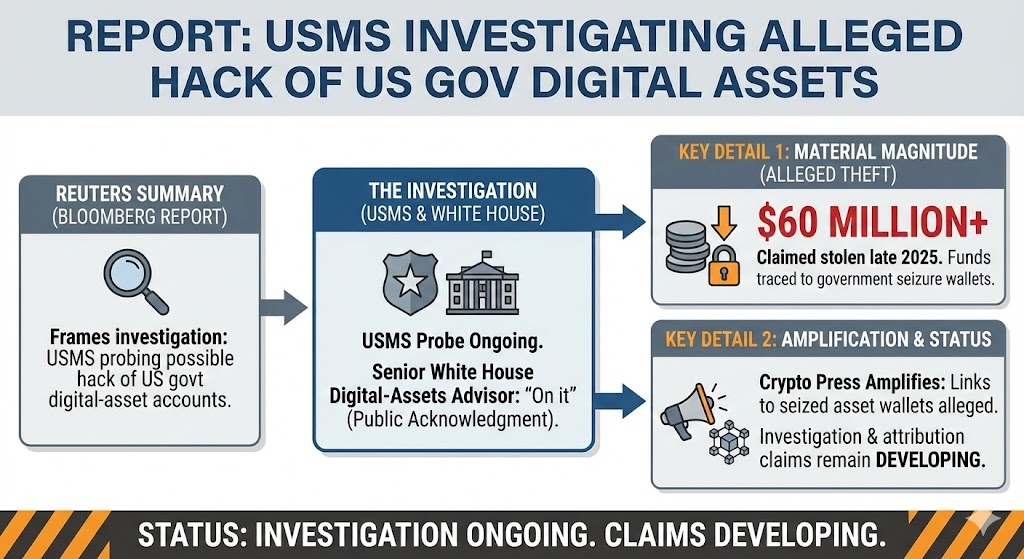
The Reuters summary of the Bloomberg report frames the investigation plainly: USMS is probing a possible hack of U.S. government digital-asset accounts.
Two details matter for investors and operators:
- The alleged theft magnitude being discussed publicly is material. Reuters notes reporting that an on-chain investigator claimed a hacker stole more than $60 million in late 2025, including funds that were traced back to government seizure wallets, and that a senior White House digital-assets advisor publicly acknowledged the claims and said he was “on it.”
- Independent crypto press has amplified the episode and described allegations that stolen funds may be linked to wallets associated with seized assets—though the investigation and attribution claims remain developing.
At this stage, investors should treat specifics—exact amounts, precise vectors, and attribution—as unconfirmed outside of what’s been publicly reported. What is confirmed is the existence of an active investigation by the U.S. Marshals Service.
Why the U.S. Marshals Service Matters in Crypto
In traditional finance, custody is boring—until it isn’t. In crypto, custody is everything.
The U.S. Marshals Service plays an unusually central role because it supports the Department of Justice Asset Forfeiture Program as a primary disbursing agency and administers the operational machinery around seized assets. That includes processes for holding and ultimately selling seized property—crypto included. Reuters explicitly notes that the USMS “oversees, secures and sells cryptocurrencies seized or forfeited in federal cases.”
That custody mandate creates a uniquely complex operational environment:
- Asset diversity: Seizures can include major coins, long-tail tokens, and assets that are difficult to liquidate or even transfer safely. A DOJ Office of Inspector General audit has previously highlighted operational challenges around certain cryptocurrency types and disposal practices.
- Chain-of-custody constraints: Evidence handling, forfeiture timelines, and court processes weren’t built for bearer assets that move globally in minutes.
- Contractor interfaces: Governments frequently rely on vendors for technical services—from custody solutions to liquidation execution—introducing classic third-party risk.
That last point is particularly sensitive because custody compromises in crypto often occur not through cryptographic failure, but through access failure: credentials, key management, insider threat, or vendor exposure.
The Macro Backdrop: 2025 Was a Record Year for Hacks and Crypto Crime Infrastructure

If this investigation feels like a “line-crossing” moment, it’s because the underlying crime environment has been compounding.
Chainalysis reports that $3.4 billion in crypto was stolen in 2025—an eye-catching number that underscores the scale of adversary capability and the profitability of attacks.
At the same time, illicit financial networks are becoming more specialized. Reuters reported Chainalysis research estimating that crypto money laundering hit at least $82 billion in 2025, fueled in part by large-scale, professionalized laundering networks.
Put those together and you get the real operational risk for 2026:
- Attacks are not only more frequent—they’re better monetized.
- Laundering has become a service industry—with escrow-like “guarantee” platforms and rapid wallet rotation.
- Targets have expanded beyond exchanges to include individuals, protocols, vendors, and custody endpoints.
In that context, government wallets are not “off-limits.” They are simply high-value targets with a different security model—and potentially, slower operational feedback loops.
The Real Story: Government Crypto Custody Is Becoming Strategic Infrastructure
The market tends to interpret government-held crypto in a narrow way: “Will they sell it?” But the deeper shift is that governments are now de facto strategic holders, managers, and market actors—even if unintentionally.
And that creates two immediate implications:
1) “Custody credibility” becomes policy-relevant
If the U.S. government wants to set standards for stablecoins, exchanges, and tokenization, it cannot afford a perception that its own crypto handling is operationally fragile. This is especially true as Washington debates broader crypto market-structure legislation and regulatory jurisdiction boundaries.
A custody incident can change the tone of that debate quickly—moving it from “innovation vs. regulation” to “operational resilience vs. systemic risk.”
2) Third-party and operational controls move to the center of valuation
Investors have historically discounted “back office” quality in crypto—until a failure forces a repricing. Over time, the crypto market has learned to price security competence (or the lack of it) into platforms, protocols, and tokens.
Now apply that lens to institutions and vendors that touch government flows—custodians, liquidity venues, forensic firms, and compliance platforms. This investigation is a reminder that operational risk is investable risk.
What an Investigation Like This Typically Examines
While USMS hasn’t disclosed investigative specifics, digital-asset compromise investigations often examine a consistent set of questions:
- Access pathways: Were private keys or signing systems directly compromised, or were credentials/social engineering involved?
- Key management model: Single-sig vs. multisig, HSM usage, segregation of duties, and approval workflows.
- Vendor and contractor permissions: Which third parties had access, directly or indirectly?
- Transaction patterning: Did the attacker consolidate funds, bridge across chains, use mixers, or route through known laundering services?
- Detection and response: How quickly did alerts trigger? Who had authority to freeze, escalate, or coordinate with exchanges?
Even without details, the existence of the probe signals that the government is treating the incident as more than a simple anomaly—and that is a meaningful stance in itself.
Market Impact: Why Investors Should Care (Even if the Dollar Amount Is “Small”)
Crypto markets can ignore a lot—until a story hits one of the ecosystem’s three pressure points: trust, access, or liquidity.
A government wallet incident touches all three.
- Trust: If seized assets can be drained, market participants will question custody processes not just at agencies, but at any entity relying on complex vendor chains.
- Access: Expect renewed scrutiny of how exchanges and off-ramps respond to flows tied to compromised wallets—especially as compliance expectations rise.
- Liquidity: If large seizure pools are perceived as vulnerable, agencies may move toward more conservative custody postures that change disposal timelines and market impact.
This also arrives at a moment when crypto is attempting to look more like mainstream finance—bank charters, regulated products, institutional rails. Headlines about compromised government accounts are the opposite of what “institutionalization” wants—but often exactly what institutionalization needs to mature.
For example, even as crypto-adjacent institutions pursue deeper integration into the regulated banking system, traditional finance is simultaneously warning about deposit and payments disruption from stablecoins—signaling that regulators and incumbents are already in a high-sensitivity mode.
The Bigger Picture: 2026’s Core Crypto Theme Is Governance, Not Just Price
Zoom out and the investigation fits a broader, investable theme for 2026:
Crypto’s next cycle is increasingly about governance, controls, and credibility—who can operate at scale without blowing up.
This applies to:
- Stablecoins (reserve transparency, yield structures, and regulatory perimeter)
- Tokenization (settlement assurance, custody, and legal enforceability)
- Market structure (agency oversight splits and licensing regimes)
- Security (institution-grade key management and incident response)
As lawmakers and regulators debate frameworks and agencies jockey for jurisdictional clarity, operational incidents can become catalysts—either accelerating reform or hardening resistance.
What to Watch Next
For investors tracking this story, four milestones matter:
- Confirmation of scope
Is this confined to one wallet cluster, or does it touch broader custody infrastructure? - Attribution and recovery path
Do investigators identify a discrete actor, an insider pathway, or a vendor compromise? Is there meaningful recovery via exchange coordination? - Policy reaction
Does this become an argument for tighter federal standards around custody and vendor oversight—possibly influencing the market-structure debate? - Operational reforms
Watch for changes in how seized assets are secured, audited, and liquidated—especially if new requirements ripple into private custodians and platforms.
Bottom Line
A “new digital asset investigation” involving U.S. government wallets is more than a headline. It’s a live test of the institutional scaffolding crypto now depends on—custody, governance, vendor controls, and investigative capacity. The market has spent years debating whether crypto should be treated like finance. Incidents like this force the harder question:
Can crypto be operated like finance—at the level where failure is unacceptable?
For 2026, that may be the most important crypto investment question of all.